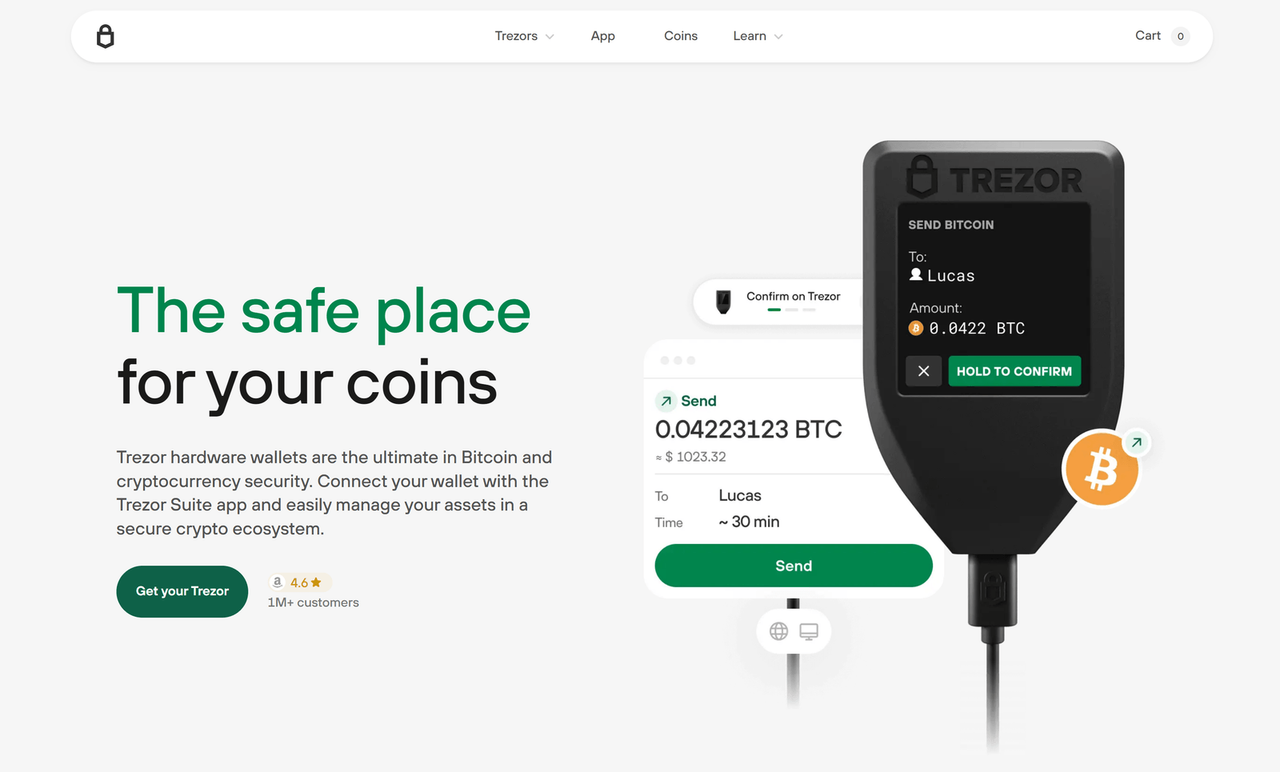
Knowing how to use Trezor securely is essential for safeguarding your cryptocurrency assets. Crypto thefts and phishing attacks are common, so understanding how to use Trezor securely ensures your private keys are protected and your funds remain safe. Whether you're storing Bitcoin, Ethereum, or other tokens, following best practices is critical.
Exploring Trezor Suite: Features You Should Know allows users to manage crypto assets efficiently. The suite includes portfolio tracking, transaction monitoring, and secure firmware updates. Recognizing Trezor Suite: Features You Should Know helps users leverage tools that simplify crypto management while maintaining top-level security.
Comparing Trezor Suite vs Other Crypto Interfaces highlights the importance of security and usability. Unlike some software wallets, Trezor Suite vs Other Crypto Interfaces emphasizes hardware-based protection, PIN access, and passphrase security, making it a more reliable choice for long-term storage.
The first step in how to use Trezor securely is proper device initialization. Always set up the device using Trezor Suite and avoid third-party software. Understanding how to use Trezor securely ensures the recovery seed is generated in a safe environment, providing a foundation for future security.
A vital aspect of how to use Trezor securely is storing your recovery seed safely. Never save it digitally or online. Proper guidance on how to use Trezor securely includes keeping the seed offline, in a fireproof safe or specialized crypto backup device, preventing unauthorized access.
For daily transactions, understanding Trezor Suite: Features You Should Know for Daily Transactions is crucial. Real-time transaction monitoring, multi-signature support, and fiat value tracking are part of Trezor Suite: Features You Should Know, ensuring convenience without compromising security.
When analyzing Trezor Suite vs Other Crypto Interfaces, security features set Trezor apart. Strong encryption, device authentication, and PIN/passphrase protection in Trezor Suite vs Other Crypto Interfaces prevent unauthorized access and reduce vulnerability to attacks compared to software-only wallets.
Adopting best practices is key in how to use Trezor securely. Keep firmware updated, always verify addresses on the Trezor screen, and avoid connecting your device to untrusted networks. These methods are the foundation of how to use Trezor securely and protect your crypto assets from potential threats.
This article provides general information about how to use Trezor securely and Trezor Suite: Features You Should Know. Cryptocurrency investments carry risk, and using hardware wallets does not guarantee complete security. Always perform your own research, follow official guidelines, and consider consulting a financial advisor before making decisions. Trezor Suite vs Other Crypto Interfaces comparisons are based on features at the time of writing and may change with software updates.
In conclusion, knowing Trezor Suite vs Other Crypto Interfaces and how to use Trezor securely empowers users to make informed choices. Utilizing the right features of Trezor Suite, protecting your recovery seed, and following best practices ensures a safe and efficient crypto experience.